
PRCCDC 2024
We are delighted to announce that OSUSEC’s Cyber Defense team won first place in PRCCDC 2024 last week!! This is our third year in a row, and we’re really looking forward to competing in …

Electronic Frontier Alliance
As OSUSEC moves into 2024 and beyond, we are taking a closer look at how our actions shape the world around us. Because of this, we are choosing to endorse the Electronic Frontier Alliance’s …

How I Approach pwn Challenges
The below write-up was posted in our internal CTF League discord server. Replicated here for posterity.
Generally, my process for a pwn challenge is:
1. Recon
- Figure out what kind of program …

Meeting 11/08/23
Ni Haowdy members!
Last night, we had our first lockpicking meeting of the school year! Zane led us through an introduction to lockpicking and the various locks we have. Lockpicking is a great outlet …

Cyberforce 2023
Last weekend, OSUSEC’s cyberdefense team flew out to Chicago to compete in the Department of Energy’s Cyberforce Competition! For 4 out of 6 members of the team, this was their very first …

Meeting 11/01/23
Happy start of winter, members!
Last night, we held a working party for the NSA Codebreaker Challenge! Lucas introduced each of the tasks and discussed the rewards for high-achievers and solvers. …
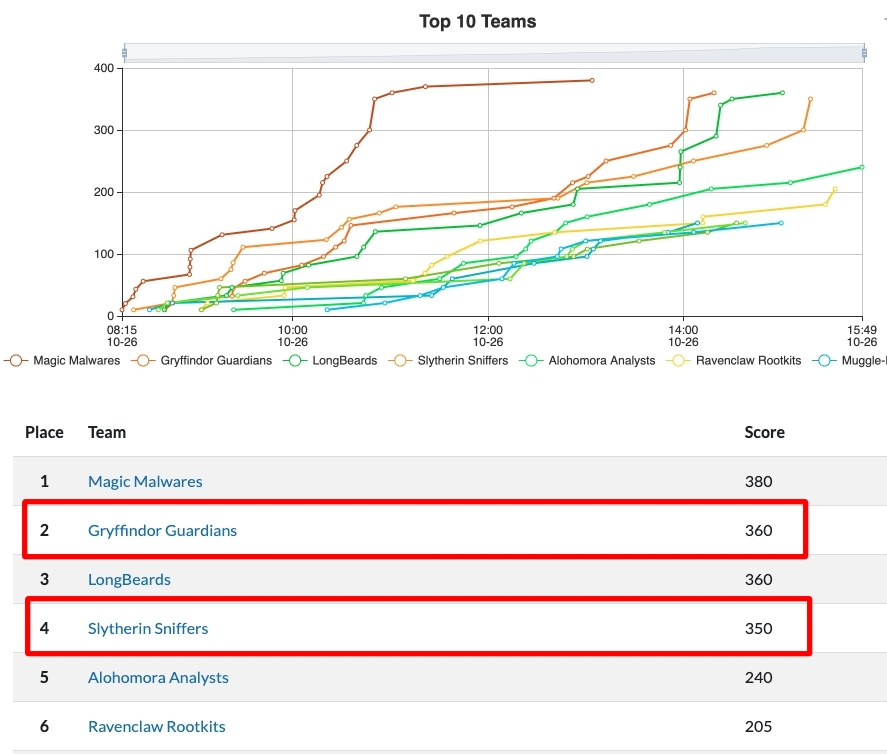
WWT Red Team CyberRange
Last Thursday, we entered two teams into WWT’s red team CyberRange! The competition tasked us with breaking into the infrastructure of a fake ransomware group. Aside from an engaging and topical …

Armis Workshop
Last Friday night, we were very fortunate to host Terry Boedeker of Armis to discuss IoT security in preparation for Cyberforce next weekend!
He talked about the importance of cyber-physical security …

Meeting 10/25/23
Good Thursday, members!
Last night we got to hear from Isabel Boona from Battelle! She presented on her work in reverse-engineering microchips, and how her previous work in materials science helped …

Meeting 10/18/23
Ni Haowdy!
Last night, we hosted Dr. Kelsey Fulton of the Colorado School of Mines. They talked about their research into the why and the how that software developers introduce security …

Meeting 10/11/23
Howdy hackers!
Last night, we had the fantastic Jonathan Keller give a talk about how he used his pwn skills in order to get a world record in a Tool Assisted Speedrun of Super Metroid! Thank you …

Meeting 10/04/23
Howdy hackers!
Thanks for showing up last night, and staying flexible with us! I know we weren’t able to host the meeting we wanted at the last minute, but hopefully you got to enjoy some memes, …
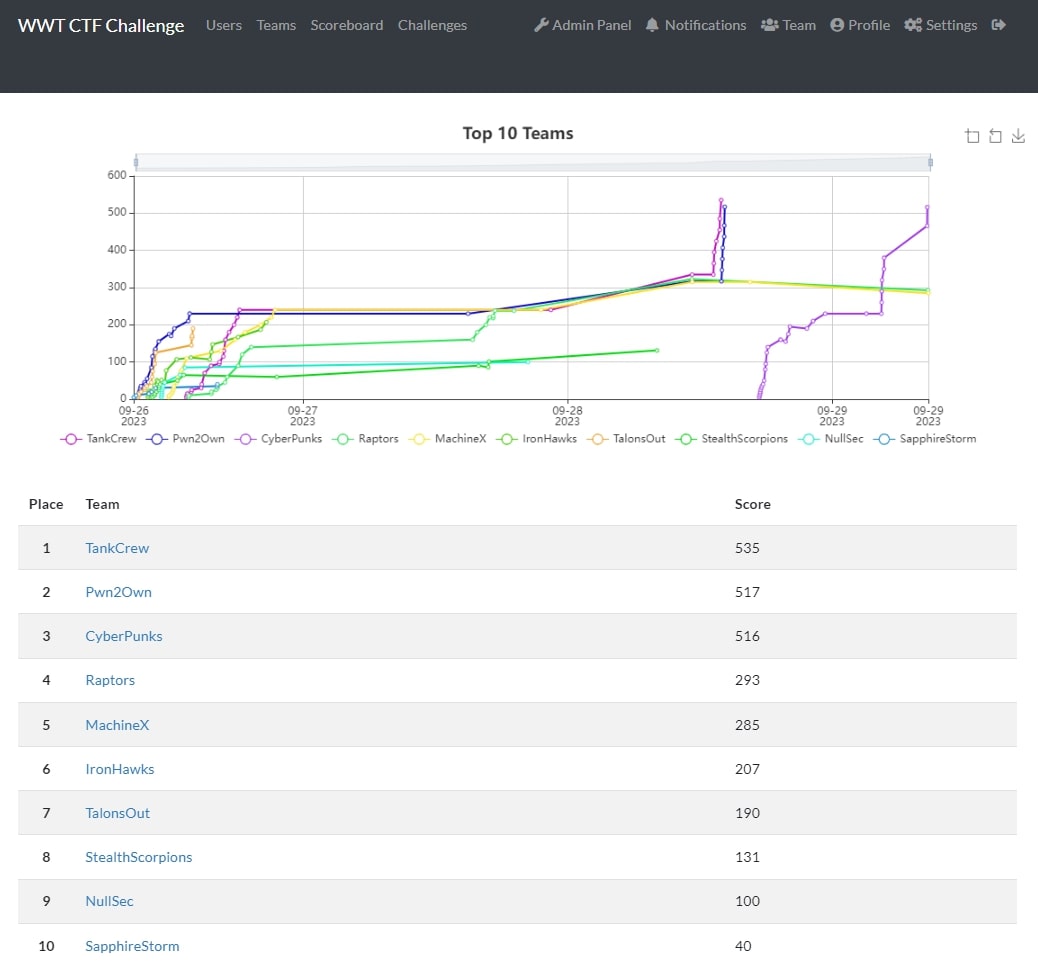
WWT Blue Team CyberRange
Last Thursday, OSUSEC assembled a team of 4 students to compete in WWT’s fantastic blue team CyberRange! We had a ton of fun and are very proud to announce that we placed 3rd, going up against a …

NCCDC 2023
The last weekend of April, OSUSEC’s Cyber Defense team competed in NCCDC, the National Collegiate Cyber Defense Competition. The competition required us to secure and administer a handful of networks …

2023-2024 OSUSEC Officers Selected
This year’s elections were intense; every candidate was subjected to memes, music, and whiteboard art that led to a lot of laughs and a lot of great people elected. Without further adieu, here are …

PRCCDC 2023
This past weekend, OSUSEC’s Cyber Defense team competed in PRCCDC, our regional Collegiate Cyber Defense Competition. The competition required us to secure and administer a handful of networks full of …

Meeting Notes 11/09
Howdy hackers! Last night, I covered cybersecurity in software development. I talked about how you can incorporate security into each stage of the Software Development Lifecycle, some examples of how …

Cyberforce Competition 2022
This past weekend, OSUSEC’s Cyberdefense Competition team flew out to Chicago, IL to compete in the Department of Energy’s Cyberforce Competition! We were tasked with securing and administering a …

Meeting Notes 11/02
Howdy hackers! Welcome to the second half of Fall term! Tonight we hosted NetSPI: Senior Director Karl Fosaaen and Security Consultant (and former club member) Michael Jereza. They walked us through …

Meeting Notes 10/19
Howdy hackers! Hope your week 4 is going well. Tonight Cameron introduced Reversed Engineering (“Rev”) challenges and how to pwn them. Rev and pwn challenges are a staple of CTF competitions, and we …

Meeting Notes 10/12
Howdy hackers! Thanks to everyone who showed up tonight! Tonight we introduced the NSA Codebreaker Challenge, and held a work party. Hopefully you were able to make some progress on Tasks in a focused …

BSidesPDX 2022
Howdy Hackers! This Friday, a group of OSUSEC members took a day trip up to Portland to attend BSidesPDX 2022 and compete in their CTF. We had an absolute blast, winning first place in the CTF, …

Meeting Notes 10/05
Howdy hackers! Thanks to everyone who showed up, and we hope it was enjoyable and informative! Tonight we introduced Cyber Defense Competitions. We covered some of the skills and areas you would learn …

Meeting Notes 9/28
Howdy hackers! Thanks to everyone who showed up to the first meeting and we hope it was fun and informative!! Tonight we helped break in the new year for the club, and many people walked away from the …

2022-2023 OSUSEC Officers Decided
The votes are in! After an entertaining election with some contested positions and contestants running from the floor, the officers for the next academic year, 2022-2023.
President: Cameron McCawley …

Meeting Notes 3/2
Thank you to everyone who attended tonight’s meeting! We talked about what Wargames are, what their value is, and what some good starter wargames are to play.
The slides for the meeting are available …

Meeting Notes 2/9
Thank you to everyone who attended tonight’s meeting! We chatted some more about reverse engineering, discussing the stack layout, function preambles and local variables on the stack. We introduced …

Meeting Notes 2/23
Thank you to everyone who attended tonight’s meeting! We introduced several different CTF categories and what challenges usually look like within those categories. Then, we went over some of the …

Meeting Notes 2/2
Thank you to everyone who attended tonight’s meeting! We chatted about reverse engineering and binary exploitation (pwn) tools and how to use them, and I demonstrated how to solve the rev01 challenge …

Meeting Notes 1/26
Thank you to everyone who attended! This meeting covered an introduction to reverse engineering on x86 64-bit. We covered some key differences between x86 and x86-64, then we examined how typical …

Meeting Notes 1/19
Thank you to everyone who attended! This meeting covered a presentation called “CS271 for Pwning”, an introduction to assembly and shellcoding with a focus on the useful aspects to pwning / binary …

Meeting Notes 1/12
Thank you to everyone who attended! This meeting covered the solutions to all NSA Codebreaker 2021 Tasks. I hope everyone enjoyed, questions can always be tossed into the #nsacc-21 channel.
Here are …

NSA Codebreaker Challenge 2021
On January 4th, 2021, OSUSEC finished 3rd place with 133,337 points at the NSA Codebreaker Challenge. 189 OSU students and OSUSEC members solved at least one of the 11 tasks, and 5 OSU students and …
DOE Cyberforce Competition 2021
On Nov. 13, 2021, the OSUSEC Cyber Defense Competition (CDC) Team placed 1st place regionally and 7th nationwide in the Department of Energy’s annual Cyberforce Competition ( …

Meeting Notes 10/27
Thank you to everyone who attended! This meeting covered an introduction to NSA Codebreaker Challenge, including some common tools and strategies used to solve challenges 0-6.
Here are the slides …

Meeting Notes 10/6
Thank you to all the members that attended this meeting! We covered lockpicking basics, legality and ethics, before Ryan presented a live demonstration of picking a lock. Then, each table had a …

Meeting Notes 10/1
Thank you to everyone for coming to our first meeting this year! We had well over our expected 70 people in attendance. We introduced OSUSEC, what we do, how our Discord server works, as well as some …

2021-2022 OSUSEC Officers Decided
For the coming school year, we welcome in 8 officers, in the following positions:
- President: Lyell Read
- Vice President: Zach Taylor
- Treasurer: Mike Carris
- Lab Manager: Cameron McCawley
- Community …

Crowdstrike Adversary Quest - Much Sad
Prompt
We have received some information that CATAPULT SPIDER has encrypted a client’s cat pictures and successfully extorted them for a ransom of 1337 Dogecoin. The client has provided the ransom …

0x41414141 CTF - 0x414141
Prompt
I think offshift promised to opensource some of their code
author: notforsale
Solution
First off, we navigate to the offshift-dev github account, linked from the offshift site. Unfortunately, …

BSidesPDX - Xclusive Numborz
Prompt
Category: Over The Air
290 Points
8 Solves
I was watching my regularly scheduled state sponsored programming when I got some strange interference. It sounded like a little girl was talking to …

BSidesPDX - Please Stand By
Prompt
Category: Over The Air
263 Points
14 Solves
Sometimes I like to tune into the TV when no shows are on so I can watch the test pattern. I like to believe that there’s a secret message hidden in …

BSidesPDX - Down the Rabbit Hole
Prompt
Category: Over The Air
297 Points
5 Solves
During one of the commercial breaks of my favorite state sponsored educational video, there was some interference once again. There was a woman …

EkoPartyCTF - Leak
EkoParty CTF 2020 Git 1
Prompt
Exact prompt has been forgotten. Linked to this GitHub repo
Solution
This solution was quite obscure, as I approached this challenge in a github mindset, not a ctf::misc …

EkoPartyCTF - Env
EkoParty CTF 2020 Git 3
Prompt
Not too sure of the original prompt, however I did not need it.
Solution
After the second part of the git challenge saga, we have gotten a new repository with some new …

EkoPartyCTF - Docs
EkoParty CTF 2020 Git 2
Prompt
Exact prompt has been forgotten. Linked to this GitHub repo
Solution
As I mentioned in the writeup for leak, I was in a very githubby mindset when I started this …

Fword CTF - Identity Fraud
Points: 419 Solves: 86 Category: OSINT
Prompt
Someone stole our logo and created a team named “Eword”. In order to find him, I created a fake twitter account (@1337bloggs) to join Eword team. …

NahamConCTF - Tron
75 points
Prompt
NahamConTronis up to more shenanigans. Find his server.
Solution
I used the namechk tools from the OSINT Framework Site. Specifically, I used OSINT Framework > Username > …

NahamConCTF - Time Keeper
50 points
Prompt
There is some interesting stuff on this website. Or at least, I thought there was…
Connect here: https://apporima.com/
Note, this flag is not in the usual format.
Solution
After …

NahamConcTF - Microosoft
100 points
Prompt
We have to use Microsoft Word at the office!? Oof…
Download the file below.
Solution
Opening the file does not do much, but it would not be that easy.
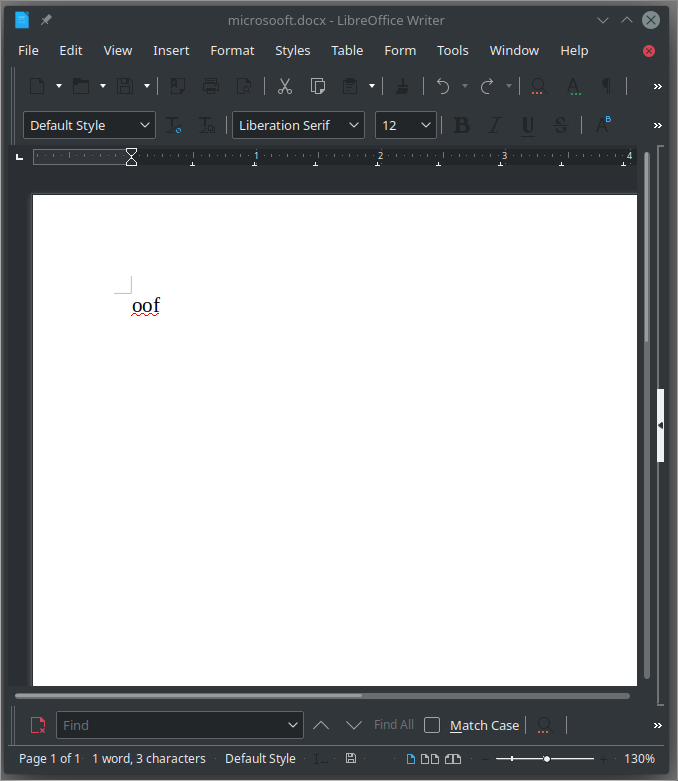
Using file we can find …

NahamConCTF - Finsta
50 points
Prompt
This time we have a username. Can you track down
NahamConTron?
Solution
I used the namechk tools from the OSINT Framework Site. Specifically, I used OSINT Framework > Username …

IJCTF - Vault Writeup
Prompt
We locked our secret box, You can directly ping the bot (@Vault #8895 ) using “start” to get the secret but we don’t know the door code we used random() also we used sleep(10).
shift register… …

HouseplantCTF Satan's Jigsaw Writeup
Prompt
Oh no! I dropped my pixels on the floor and they’re all muddled up! It’s going to take me years to sort all 90,000 of these again 🙁
Dev: Tom
Hint! long_to_bytes
File: chall.7z
Solution
This …

HouseplantCTF - Catography Writeup
Prompt
Jubie’s released her own collection of cat pictures. Go check it out!
http://challs.houseplant.riceteacatpanda.wtf:30002
Note: The Unsplash author credit is not a part of the challenge, it’s …

PRCCDC 2020 Results
Due to the current COVID-19 pandemic, the in-person Pacific Rim Collegiate Cyber Defense Competition (PRCCDC) was unfortunately cancelled. However, PRCCDC, working in combination with NCCDC, allowed …

ByteBanditsCTF - string.equals(integer) Writeup
Prompt
Someone gave me two functions to convert strings into integers. I converted some strings to the integers and noted them down. Can you help me converting the concatenation of those strings in …

MidnightsunCTF Snake++
Prompt
141 points, 38 solves
Snake Oil Co. has invented a special programming language to play their new and improved version of Snake. Beat the game to get the flag. settings Service: nc …

AUCTF - Who Made Me
950 points
Prompt
One of the developers of this CTF worked really hard on this challenge.
note: the answer is not the author’s name
Author: c
Solution:
Now for a much more real-world OSINT …

AUCTF - OSINT You All Over the Place
A post-competition writeup; 983 points
Prompt
I do not have access to the prompt, but the URL is devs-r-us.xyz
Solution
After solving the first three challenges, I looked into this one. I investigated …

AUCTF - Good Old Days
877 points
Prompt
This site used to look a lot cooler.
Author: c
Solution
Wayback Machine, here I come! This is the most useful view of the captures for the site ctf.auburn.edu: …

AUCTF - ALIedAS About Some Thing
903 points
Prompt
See what you can find.
AUCTFShh
Author: c
Solution
AUCTFShh looks like a username. To find where that username is in use, we can either check manually (as I started out doing), or …

NahamConCTF - Fake File
100 points
Prompt
Wait… where is the flag?
Connect here: nc jh2i.com 50026
Solution
Let’s nc to that server and see what’s up:
$ nc jh2i.com 50026
bash: cannot set terminal process group (1): …
VolgaCTF - excellent-crackme
Prompt
Excellent Crackme We know one can do pretty much everything in Excel spreadsheets, but this…
Solution
An excel challenge – that’s a first for us! Let’s crack that file open. We …

TAMUCTF RSAPWN
Prompt
We must train the next generation of hackers.
nc challenges.tamuctf.com 8573
Solution
It looks like this just asks us to find the two “big prime” factors of the number provided, and return …

TAMUCTF - WOOF_WOOF
Prompt
(I did not get the prompt text in time, and admin closed access to the challs when the CTF ended :()
The instructions mentioned charset A-Z and ‘-‘ and ‘@’, with flag format GIGEM-.... …

TAMUCTF - RUSSIAN_NESTING_DOLLS
Prompt
Our monitoring systems noticed some funny-looking DNS traffic on one of our computers. We have the network logs from around the time of the incident. Want to take a look?
Files: netlogs.pcap …

TAMUCTF - GEOGRAPHY
Prompt
My friend told me that she found something cool on the Internet, but all she sent me was 11000010100011000111111111101110 and 11000001100101000011101111011111.
She’s always been a bit cryptic. …

TAMUCTF - ALCAPONE
Prompt
Eliot Ness is the lead on taking down Al Capone. He has gained access to Capone’s personal computer but being the good detective he is, he got the disk image of the computer rather than look …

FireshellCTF Against the Perfect discord Inquisitor 1 and 2
Prompt 1
You’re on a journey and come to the Tavern of a Kingdom Enemy, you need to get information of a secret organization for the next quest. Be careful about the Inquisitor! He can ban you from …

Officer Elections on 3/12
Next week, we will be having officer elections! This is a great way to get more involved with the club and help represent the College of Engineering. tl;dr Come vote on Thursday, 3/12 at 7pm in KEC …

Meeting Notes 10/3
Thanks for the great turnout again tonight! We went over some tools you can use for the NSA Codebreaker challenge.
Here is a link to the slides (requires ONID sign-in): Google Slides
Next week’s CTF …

Meeting Notes 9/26
Thanks everyone for coming out to our first meeting! We had over 50 people in attendance, and introduced the OSU Security Club, what we do, what we stand for, our plans for the year, and worked on a …

DefCon Qualifiers 2019 - redacted-puzzle
The only file given is a GIF image, named redacted-puzzle.gif. We must first inspect it:
$ exiftool redacted-puzzle.gif
ExifTool Version Number : 10.80
File Name : …
Meeting Notes 5/9
Today we hosted Ryan Gurr and Alex Ryan from Fidelis Cybersecurity, who talked about their experiences and background in information security, and showed a cool demo of Fidelis’s platform.
If you have …

ångstromCTF lithp
Problem
My friend gave me this program but I couldn’t understand what he was saying – what was he trying to tell me?
Author: fireholder
Points: 60
Solution
First things first, let’s open that lisp …

ångstromCTF - streams
Problem
White noise is useful whether you are trying to sleep, relaxing, or concentrating on writing papers. Find some natural white noise here.
Note: The flag is all lowercase and follows the …

2019-2020 Officers
Here are the new officers for the 2019-2020 school year:
- President: Zander Work
- Vice President: Hadi Rahal-Arabi
- Treasurer: David Park
- Multimedia Coordinator: Adam Stewart
- Lab Manager: Ryan Kennedy …

Meeting Notes 4/18
Tonight I gave a tutorial on IDA Pro basics, and how to get started with this awesome tool. I also released some new binaries on the CTF site for you to practice IDA.
Remember, as a OSU Security Club …

2019-2020 Officer Elections on April 25th
We will be holding officer elections for next school year during our regular meeting on Week 4 (April 25th). This is a great way to be more involved with the club, and represent us to the College of …

PRCCDC 2019 Results
This past weekend, OSUSEC competed at the Pacific Rim Collegiate Cyber Defense Competition (PRCCDC) hosted by Highline College. I’m pleased to announce that we placed 3rd out of 13 teams in this tough …

UTCTF 2019 - Scrambled
Tl;dr Cool encoding using Rubik’s cube, I wrote a Python script.
This was a 1250 point Forensics challenge (highest points in the category). Here’s the description:
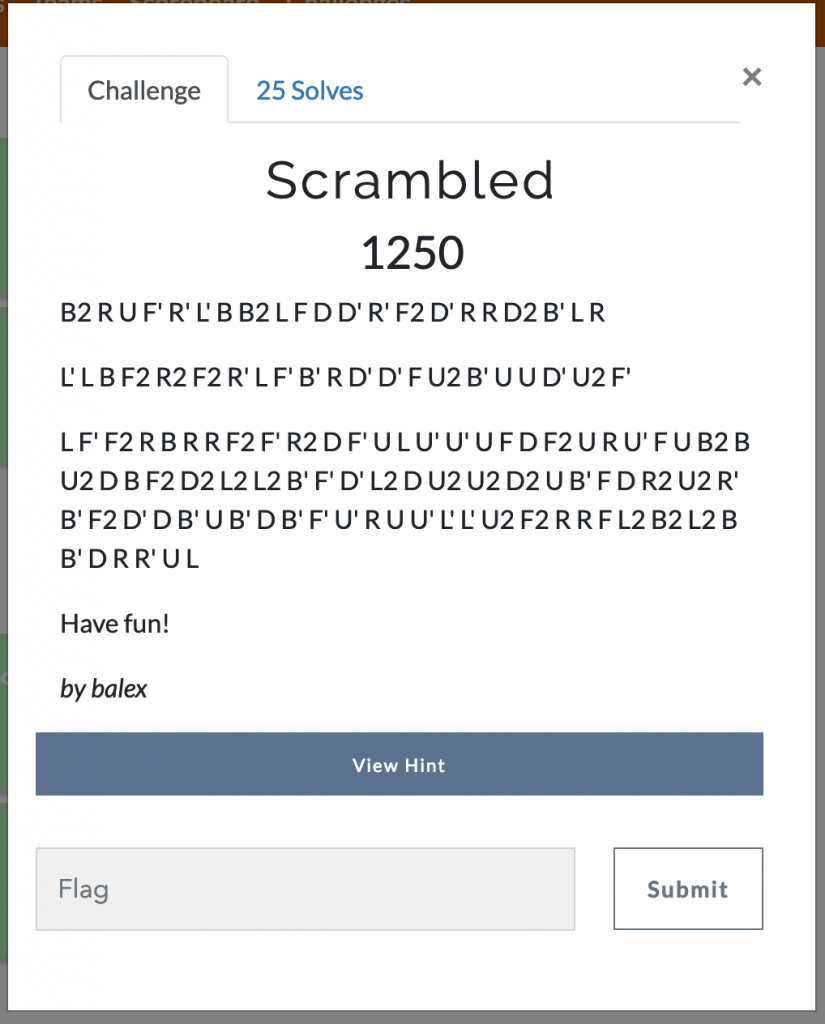
By the time I took a look at the …

UTCTF 2019 - Crackme
This was a 1200 point reversing challenge (tied for highest point value in the category). Here’s the description:
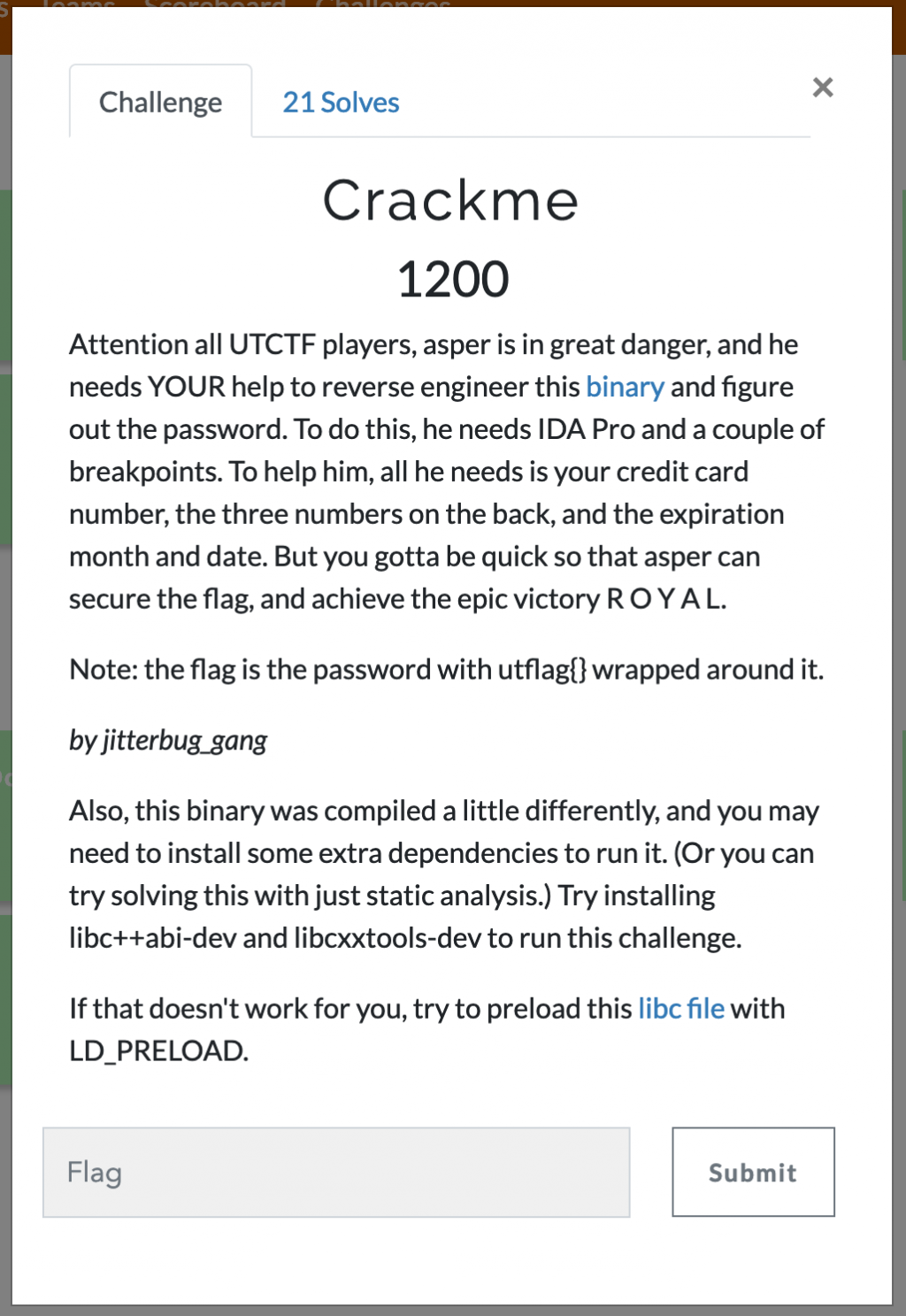
This what we see when we run the binary:
$ ./crackme
Please enter the correct …
UTCTF 2019 - Rogue Leader
Problem Description
Our once-venerable president has committed the unspeakable crime of dine-and-dashing the pizza during our own club meetings. He’s on the run as we speak, but we’re not sure where …

Meeting Notes - 3/7
Thanks to Kees Cook for an awesome look at kernel security! Kees talked about how the kernel exploit for CVE-2017-7038 was discovered, which allowed privilege escalation due to a heap overflow.
You …

Meeting 2/28 - OSUSEC Lab
Tonight I talked about the new OSUSEC lab environment! A few systems are currently live, and more will be coming up through the end of the term, including the self-registration system. For information …

Meeting 2/21
Tonight we hosted Karl Fosaaen from NetSPI, and he gave an awesome talk on pentesting in an Azure environment.
If you’re interested in learning more about this, check out the NetSPI blog or the Azure …

Meeting 2/14
Tonight I went over some basic usage of GDB, IDA Pro, and pwntools for solving the first pwnables on our CTF site.
Link to the slides (requires ONID login). The slides have information on getting the …

Meeting 2/7
Today we continued discussing reverse engineering and introduced 64-bit assembly. There are more samples on the GitHub repo.
The only announcement for today is to RSVP for our upcoming event with …

Meeting 1/31
Today we talked about some basic reverse engineering, and compare/contrasting x86 assembly with C code.
There are some new challenges up on CTFd, rev[1-4]

Meeting 1/24
Tonight we worked on buffer overflows, and some binaries on the new OSUSEC CTF platform.
Next week, we’re going to work on similar binaries, but comparing the assembly …

Meeting 1/17
Tonight we talked about some CTF tools and did a walkthrough for “start” on pwnable.tw. You can read a detailed writeup for this binary on the OSUSEC GitHub.
Here’s a link to the slides (requires ONID …

NSA Codebreaker 2018 Task 7
Refunds – (Smart-Contract Development; Vulnerability Analysis; Exploit Development)
Task 7 has us refund the victims who have already paid the ransom. In other words, we need to recover all the funds …

NSA Codebreaker 2018 - Task 6
Loophole – (Smart-Contract Development; Vulnerability Analysis; Exploit Development)
Task 6 has us exploit a loophole in the smart-contracts to recover the decryption key without spending any ether …

Meeting 1/10
Thanks for a great first meeting for Winter 2019!
Here is a link to the slides (requires ONID login): Slides
For those of you who were unable to make it, here’s a brief summary of what we went over. …

Welcome to Winter 2019!
Happy New Years! Our first meeting will be this Thursday at 7pm in KEC1003, and we will be meeting at the same time/place the whole term.
Some things to look forward to for this term:
I’m working with …
NSA Codebreaker Challenge 2018 Results
The NSA Codebreaker Challenge finished today, and I’m proud to announce that Oregon State University is the winner! We also had the most people complete Task 5 and 2 people complete Task 7, which is …

Cyberforce Competition 2018 Results
I’m thrilled to announce that OSUSEC placed 1st at the Cyberforce Competition last weekend at PNNL, and 3rd nationwide out of 70 teams! I’m very proud of everyone’s hard work, and am already excited …

Meeting 11/15
Thanks for a great last meeting for the Fall term!
I gave a talk on all of the low-level architecture and x86 assembly content needed to get started with binary pwning, here is a link to the slides. …

Meeting 11/01
Thanks to Karl Fosaaen from NetSPI for the awesome presentation on an introduction to penetration testing! Remember, if you want to learn about these things on your own, please make sure to do it on …

Meeting 10/25
Thanks to Emily for the great talk on SIEMs (Security Incident and Event Management)! Here is a link to the slides.
Announcements from tonight’s meeting:
- Make sure to RSVP for the NetSPI event …

HITCON CTF 2018 EV3 Basic
Even though this was a pretty simple challenge, I really enjoyed it and wanted to do a write-up for it anyways.
EV3 is the latest generation of the LEGO Mindstorms robots, and thanks …

Meeting 10/11
Thanks Zach for the awesome presentation tonight on Network Security Monitoring! I’ll update this post with a link to the slides once they are available.
Announcements from tonight’s meeting:
Make …
Meeting 10/4
Thanks to Akshith for a great presentation on Blockchain! For those of you who were unable to make it, here is a link to the slides: …

Meeting 9/27
Thanks for the awesome turnout tonight! I’ll make a permanent reservation for that space, as it seems like we have a lot more members this year, which is fantastic!
Here is a link to the slides for …

Cyberforce Competition
The Cyberforce Competition (formerly known as the Department of Energy Cyber Defense Competition) is coming up in a couple months, and it’s time to start getting ready!
If you are interested in being …

Osusec Wins Department of Energy Cyber Defense Competition
Over the past weekend, OSUSEC competed in the Department of Energy Cyber Defense Competition (DOE CDC), and placed 1st regionally (US West), and 4th nationwide. The team was responsible for deploying …



